반응형
https://dreamhack.io/wargame/challenges/830
🌱 simple-web-request
Description STEP 1~2를 거쳐 FLAG 페이지에 도달하면 플래그가 출력됩니다. 모든 단계를 통과하여 플래그를 획득하세요. 플래그는 flag.txt 파일과 FLAG 변수에 있습니다. 플래그 형식은 DH{...} 입니다. 📜
dreamhack.io
문제
STEP 1~2를 거쳐 FLAG 페이지에 도달하면 플래그가 출력됩니다.
모든 단계를 통과하여 플래그를 획득하세요. 플래그는 flag.txt 파일과 FLAG 변수에 있습니다.
플래그 형식은 DH{…} 입니다.
풀이
문제 파일을 읽을 수만 있으면 바로 해결되는 문제
@app.route("/step1", methods=["GET", "POST"])
def step1():
if request.method == "GET":
prm1 = request.args.get("param", "")
prm2 = request.args.get("param2", "")
step1_text = "param : " + prm1 + "\nparam2 : " + prm2 + "\n"
if prm1 == "getget" and prm2 == "rerequest":
return redirect(url_for("step2", prev_step_num = step1_num))
return render_template("step1.html", text = step1_text)
else:
return render_template("step1.html", text = "Not POST")prm1에 getget, prm2에 rerequest를 넣으면 step2로 이동한다고 한다
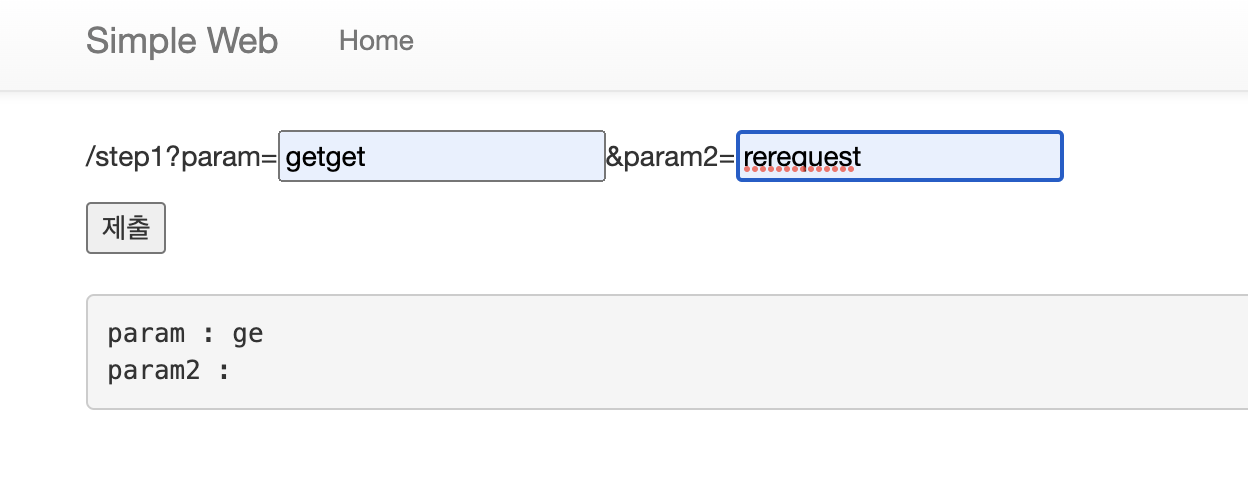
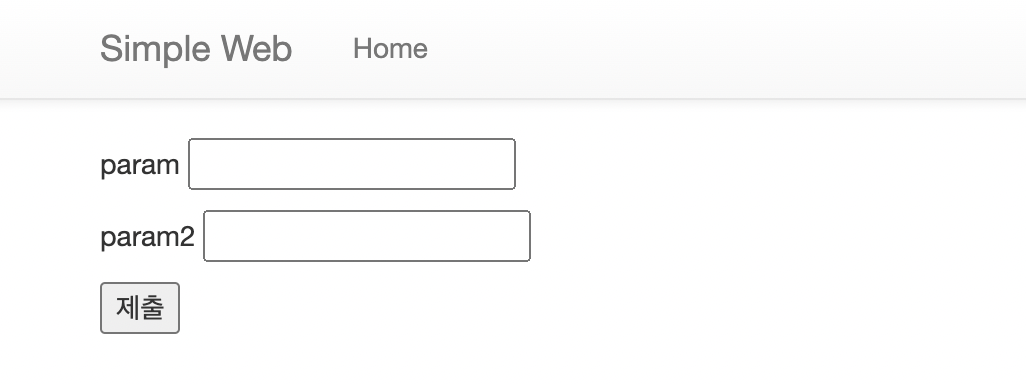
와! 이동했다 !
@app.route("/flag", methods=["GET", "POST"])
def flag():
if request.method == "GET":
return render_template("flag.html", flag_txt="Not yet")
else:
prm1 = request.form.get("param", "")
prm2 = request.form.get("param2", "")
if prm1 == "pooost" and prm2 == "requeeest":
return render_template("flag.html", flag_txt=FLAG)
else:
return redirect(url_for("step2", prev_step_num = str(step1_num)))
return render_template("flag.html", flag_txt="Not yet")
except:
return render_template("flag.html", flag_txt="Not yet")
이쪽 또한 코드에 나와있는대로 pooost 와 requeeest를 입력하면

답 플래그가 출력된다
반응형
'🔒 CTF (Dreamhack) > Web Hacking (웹해킹)' 카테고리의 다른 글
| [DreamHack] 드림핵 웹해킹 : session (0) | 2023.09.11 |
|---|---|
| [DreamHack] 드림핵 웹해킹 : pathtraversal (0) | 2023.08.14 |
| [DreamHack] 드림핵 웹해킹 : blind-command (0) | 2023.07.31 |
| [DreamHack] 드림핵 웹해킹 : Carve Party (0) | 2023.07.27 |
| [DreamHack] 드림핵 웹해킹: web-ssrf (0) | 2023.07.17 |